|
By Stu Sjouwerman
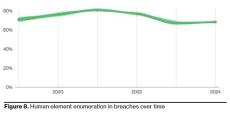
Regardless of whether your environment is on-premises, in the cloud or hybrid, new data makes it clear that users are the top cybersecurity concern, and we cover what you can do about it. According to Netwrix’s 2024 Hybrid Security Trends Report, 79% of organizations experience one or more security incidents in the last 12 months. This is a 16% increase from the previous year, demonstrating that attacks are not subsiding one bit and that they are increasingly successful.
|
By Stu Sjouwerman
Despite growing security investments in prevention, detection and response to threats, users are still making uninformed mistakes and causing breaches. One of the basic tenets of KnowBe4 is that your users provide the organization with an opportunity to have a material (and hopefully positive) impact on a cyber attack. They are the ones clicking malicious links, opening unknown attachments, providing company credentials on impersonated websites and falling for social engineering scams of all kinds.
|
By Roger Grimes
Rapid7 reports an interesting social engineering scheme that easily bypasses content filtering defenses and creatively uses a fake help desk to supposedly “help” users put down the attack. The Black Basta ransomware group, also covered in a recent CISA warning bulletin, floods a victim’s email inbox with many, many emails. The emails are often otherwise legitimate emails, such as newsletter confirmation emails, which most email content filtering gateways would not block.
|
By Stu Sjouwerman
A scam operation called “Estate” has attempted to trick nearly a hundred thousand people into handing over multi-factor authentication codes over the past year, according to Zack Whittaker at TechCrunch. The scammers target users of Amazon, Bank of America, Capital One, Chase, Coinbase, Instagram, Mastercard, PayPal, Venmo, Yahoo and more.
|
By Stu Sjouwerman
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve their social engineering attacks. “AI provides augmented and enhanced capabilities to schemes that attackers already use and increases cyber-attack speed, scale, and automation,” the FBI says.
|
By Stu Sjouwerman
New data shows that despite the massive evolution of the cybercrime economy, threat actors are sticking with the basics in social engineering attacks, with a goal at stealing data. I probably could have called this purely based on all the articles I’ve written (and all the articles I’ve read that never made it here). But when it comes to protecting your organization from social engineering, stick to the basics.
|
By Stu Sjouwerman
New analysis of Q1’s ransomware attacks uncovers a single group responsible for the majority and discusses what makes them so successful. This sort of analysis helps to establish threat landscape trends and keeps our collective focus on the places where cyber attacks are working.
|
By Stu Sjouwerman
Attackers are exploiting Reflected Cross-Site Scripting (XSS) flaws to bypass security filters, according to a new report from Vipre. This technique allows attackers to send benign links in phishing emails that will redirect users to malicious sites. Vipre also found that attackers are increasingly using links instead of malicious attachments in their phishing emails. “Three years ago, it was a 50/50 split between phishing emails utilizing links versus attachments,” the researchers write.
|
By Stu Sjouwerman
Trend analysis of ransomware attacks in the first quarter of this year reveals a continual increase in the number of "unknown" initial attack vectors, and I think I might understand why. There are two reports that you should be keeping an eye on—the updated Verizon Data Breach Report and ransomware response vendor Coveware’s Quarterly Ransomware Reports. In their latest report covering Q1 of this year, we see a continuing upward trend in “unknown” as the top initial attack vector.
|
By Stu Sjouwerman
Just when you think bad actors cannot sink any lower, they find a way to. In a recent chilling evolution of ransomware tactics, attackers are now also targeting the families of corporate executives to force compliance and payment. Mandiant's Chief Technology Officer, Charles Carmakal, highlighted this disturbing trend at RSA last week: criminals engaging in SIM swapping attacks against executives' children.
|
By KnowBe4
"Reality Hijacked" isn't just a title — it's a wake-up call. The advent and acceleration of GenAI is redefining our relationship with “reality” and challenging our grip on the truth. Our world is under attack by synthetic media. We’ve entered a new era of ease for digital deceptions: from scams to virtual kidnappings to mind-bending mass disinformation. Experience the unnerving power of AI that blurs the lines between truth and fiction.
|
By KnowBe4
Check out the blog post: https://blog.knowbe4.com/ai-does-not-scare-me
|
By KnowBe4
As an InfoSec professional, one of your important responsibilities is to minimize expensive downtime and prevent data breaches. Skyrocketing ransomware infections can shut down your network and exfiltrate data. Phishing is responsible for two‑thirds of ransomware infections. You know this and need help articulating the value of KnowBe4 to your CFO and leadership. This guide showcases real ROI experienced by KnowBe4 customers to help you present a strong business case for the investment.
|
By KnowBe4
Need holiday tips to keep your users cyber safe this holiday season? Not to fear, our KnowBe4 Security Awareness Advocates Erich Kron and Javvad are here to help! They share five helpful holiday cyber safety tips that you can share with your users.
|
By KnowBe4
PhishER Plus was developed to help you supercharge your organization’s email security defenses and is an additional final layer after your existing SEG and other cybersecurity layers fail. See what the Global Blocklist capability can do - Blocklist entries of validated threats crowdsourced from 10+ million trained users are leveraged to automatically block matching new incoming messages from reaching your users’ inboxes. This continually updated threat feed is managed by KnowBe4 and syncs with your Microsoft 365 mail server.
|
By KnowBe4
In the mystical realm of cyberspace, where digital forests hold secrets and virtual owls deliver messages, we find ourselves in a constant dance between magic and deception. Today, KnowBe4's Security Awareness Advocate Anna Collard will unveil the secrets of spear phishing.
The Role of AI in Email Security and How Real-Time Threat Intelligence Can Supercharge Your SOC Team
|
By KnowBe4
In response to improved email security measures, cybercriminals have pivoted to more advanced attack methods, namely artificial intelligence (AI), that bypass existing protections. But security defenders are also using AI in remarkable new ways to fortify their networks. Join Erich Kron, Security Awareness Advocate for KnowBe4, and Michael Sampson, Principal Analyst at Osterman Research, as they dig into the findings of our latest joint report on The Role of AI in Email Security. They’ll share tips on how your SOC team can identify and use AI to supercharge your anti-phishing defense.
|
By KnowBe4
They are out there, watching and waiting for an opportunity to strike; the bad actors who have carefully researched your organization in order to set the perfect trap using easily found public resources. Open-Source Intelligence (OSINT) can provide cybercriminals everything they need to know to perfectly target your users by gathering data on everything from password clues to tech stack details, banking/credit card accounts, social media details and more. Emerging technologies like AI can make gathering this intelligence even easier.
|
By KnowBe4
Cyber-Monsters beware! In this week's cyber-monsters blog edition, KnowBe4's Security Awareness Advocate Jacqueline Jayne discusses how Count Hackula could be waiting in the shadows to bite on your weak or reused password.
|
By KnowBe4
Imagine an artificial intelligence (AI) system developed by a mad scientist to leverage the full capabilities of Large-Language-Models (LLM). Then, the scientist went truly mad by utilizing text, voice, and video generation paired with mutating and self-perpetuating malware, as well as continuous improvement through reinforcement learning. The concoction you would get from the scientist’s wild lab is called Frankenphisher, the most effective social engineering AI you can possibly imagine.
|
By KnowBe4
Your employees are your largest attack surface. For too long the human component of cybersecurity has been neglected, leaving employees vulnerable and creating an easy target for cybercriminals to exploit. But your users want to do the right thing. Rather than a hurdle to be overcome, organizations need to think of their employee base as an asset, once properly equipped.
|
By KnowBe4
Want to read this bestseller? Register now for your free (instant 240-page PDF download) Cyberheist e-book and learn how to not be the next victim! Cyberheist was fully updated and written for the IT team and owners / management of Small and Medium Enterprise, which includes non-profits, local and state government, churches, and any other organization with more than a few thousand dollars in their bank operating account.
|
By KnowBe4
Spear phishing emails remain a top attack vector for cybercriminals, yet most companies still don't have an effective strategy to stop them. This enormous security gap leaves you open to business email compromise, session hijacking, ransomware and more. Don't get caught in a phishing net! Learn how to avoid having your end users take the bait. Roger Grimes, KnowBe4's Data-Driven Defense Evangelist, will cover techniques you can implement now to minimize cybersecurity risk due to phishing and social engineering attacks.
|
By KnowBe4
Hackers have become increasingly savvy at launching specialized attacks that target your users by tapping into their fears, hopes, and biases to get access to their data. Cybersecurity is not just a technological challenge, but increasingly a social and behavioral one. People, no matter their tech savviness, are often duped by social engineer scams, like CEO fraud, because of their familiarity and immediacy factors.
|
By KnowBe4
All multi-factor authentication (MFA) mechanisms can be compromised, and in some cases, it's as simple as sending a traditional phishing email. Want to know how to defend against MFA hacks? This eBook covers over a dozen different ways to hack various types of MFA and how to defend against those attacks.
|
By KnowBe4
Anything but 100% completion on your employee compliance training is often more than simply frustrating. Compliance audits and regulatory requirements can make anything less than 100% feel like a failure. But, getting compliance on your compliance training is possible! Organizations have struggled for years with getting everyone to complete their required compliance training. This puts organizations at risk of more incidents occurring, fines or reputational damage if an employee is non-compliant.
- May 2024 (24)
- April 2024 (34)
- March 2024 (38)
- February 2024 (42)
- January 2024 (46)
- December 2023 (41)
- November 2023 (33)
- October 2023 (45)
- September 2023 (49)
- August 2023 (49)
- July 2023 (42)
- June 2023 (45)
- May 2023 (48)
- April 2023 (44)
- March 2023 (14)
- February 2023 (3)
- January 2023 (4)
- December 2022 (3)
KnowBe4 is the provider of the world's largest integrated platform for security awareness training combined with simulated phishing attacks. Join our more than 56,000 customers to manage the continuing problem of social engineering.
The KnowBe4 platform is user-friendly and intuitive, and powerful. It was built to scale for busy IT pros that have 16 other fires to put out. Our goal was to design a full-featured, yet easy-to-use platform.
Find Out How Effective Our Security Awareness Training Is:
- Train Your Users: The world’s largest library of security awareness training content. Automated training campaigns with scheduled reminder emails.
- Phish Your Users: Best-in-class, fully automated simulated phishing attacks, thousands of templates with unlimited usage, and community phishing templates.
- See The Results: Enterprise-strength reporting, showing stats and graphs for both training and phishing, ready for management. Show the great ROI!
Human Error. Conquered.